Difference between revisions of "Policy:Ping Response Policy Page"
m (Update for Ping) |
m (Finish the sentence) |
||
| (2 intermediate revisions by the same user not shown) | |||
| Line 3: | Line 3: | ||
== Overview == | == Overview == | ||
| + | |||
| + | The 'Ping response' policy enables you to run the Ping command from a Veloopti agent to a DNS Name or IP Address of your choice. The Ping command can be performed one ore more times with the cumulative responses composing the Policy response. | ||
A policy is an instructions run on one or more of your monitored servers looking for an event that could lead to loss of, or disruption to, an organisation's operations, services or functions. Each policy is found in an application | A policy is an instructions run on one or more of your monitored servers looking for an event that could lead to loss of, or disruption to, an organisation's operations, services or functions. Each policy is found in an application | ||
A [[policy|policy]] is represented in Veloopti by the policy icon: <sup>[[file:icon_policy.png|30px]]</sup> | A [[policy|policy]] is represented in Veloopti by the policy icon: <sup>[[file:icon_policy.png|30px]]</sup> | ||
| − | |||
| − | |||
Ping response policies must be added to a [[Group|Policy Group]] for automated deployment onto one or more managed nodes. | Ping response policies must be added to a [[Group|Policy Group]] for automated deployment onto one or more managed nodes. | ||
| Line 14: | Line 14: | ||
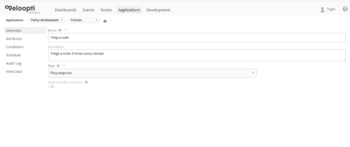
[[File:Ping response page.png|thumb|350px|The Ping Response policy page is found by selecting a policy from the policy view.]] | [[File:Ping response page.png|thumb|350px|The Ping Response policy page is found by selecting a policy from the policy view.]] | ||
| − | Ping Response policies are created and edited from within an [[Application|application]]. A policy is only visible from within the application that it was created in. After entering an application select 'Policies' from the application breadcrumb to view the . | + | Ping Response policies are created and edited from within an [[Application|application]]. A policy is only visible from within the application that it was created in. After entering an application select 'Policies' from the application breadcrumb to view the list of policies that are available in the application. |
# Click on the Application menu item | # Click on the Application menu item | ||
| Line 115: | Line 115: | ||
::'''Basic''' Select "Minutes" or "Hours" and type when on the minute or hour the policy should run. | ::'''Basic''' Select "Minutes" or "Hours" and type when on the minute or hour the policy should run. | ||
::'''Time of day''' Select hour and minute and the weekday(s) that the policy should run. | ::'''Time of day''' Select hour and minute and the weekday(s) that the policy should run. | ||
| − | ::'''Custom''' Select "Minutes" or "Hours" and type when on the minute or hour the policy should run. Select the time range when the policy should be active: e.g. 9:00am - 5:00pm. | + | ::'''Custom''' Select "Minutes" or "Hours" and type when on the minute or hour the policy should run. Select the time range when the policy should be active: e.g. 9:00am - 5:00pm. Select the weekday(s) that the policy should run. |
| − | |||
=== Audit Log === | === Audit Log === | ||
Latest revision as of 17:17, 14 November 2021
Home > Using > Web User Interface > Views > Ping response policy
Contents
1 Overview
The 'Ping response' policy enables you to run the Ping command from a Veloopti agent to a DNS Name or IP Address of your choice. The Ping command can be performed one ore more times with the cumulative responses composing the Policy response.
A policy is an instructions run on one or more of your monitored servers looking for an event that could lead to loss of, or disruption to, an organisation's operations, services or functions. Each policy is found in an application
A policy is represented in Veloopti by the policy icon: ![]()
Ping response policies must be added to a Policy Group for automated deployment onto one or more managed nodes.
1.1 Creating or editing a policy
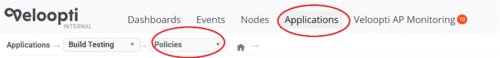
Ping Response policies are created and edited from within an application. A policy is only visible from within the application that it was created in. After entering an application select 'Policies' from the application breadcrumb to view the list of policies that are available in the application.
- Click on the Application menu item
- Click on the Application
- Select the Policies breadcrumb as shown below to view the Policy view
- From here you can either click on the Policy Wizard to create a new Policy or select a ping Response policy to modify it.
Tabs run down the left hand side of the view. Clicking on a tab will change the page that allows for a particular part of the policy to be modified. They are: Overview, Attributes, Conditions, Node Overrides, Schedule, Audit Log and View Data.
2.1 Ping Response Policy Page
NAME The title of the policy that can be used to tell the policy apart from others
DESCRIPTION Describes the policy and explains what it does
TYPE Ping Response
NODE OVERRIDES CONDITIONS Enabling this slider makes the Node Overrides tab visible.
2.2 Attributes
HOST The full DNS name or IP address that is to have the ping sent to it.
PACKET COUNT The number of times to send the ping command to the Host
TIMEOUT Timeout in milliseconds to wait for each ping reply.
2.3 Conditions
Either add a new row by clicking on the [Add] button or click on an existing row to enter the edit condition dialogue box. The rules may be moved up and down by selecting and holding the rule to change its position. Click on the [Add] button to bring up the dialogue to add a condition to the policy.
NOTE: Currently changing the position of order of the rules does not do anything as they are evaluated in order of severity.
- EVALUATE
- Metric Select a metric upon which to perform a threshold evaluation. The options available are:
- Minimum round-trip delay time
- Maximum round-trip delay time
- Average round-trip delay time
- Time to Live (TTL)
- Percent Loss
- Metric Select a metric upon which to perform a threshold evaluation. The options available are:
- EVALUATE
- OperatorSelect an operator to perform against the Metric above. Different options are available for different metrics.
- Equals
- Less than
- Less than or equal to
- Greater than or equal to
- Greater than
- Does not equal
- OperatorSelect an operator to perform against the Metric above. Different options are available for different metrics.
- Value Enter a value to compare the metric against using the operator.
- BREACH AND RESET
- Breach duration Enter the number of consecutive breaches that need to occur for an event to be raised. Note this is breaches for a policy run, not individual ping failures.
- BREACH AND RESET
- Reset Duration Enter the number of consecutive successful policy runs, the number that the metric must be (usually) below, for the event severity to be set to Normal. Note this for successful policy nuns, not successful individual pings.
- CREATE EVENT
- Event Severity The severity that appears on the event that is raised by a threshold violation of the rule
- Event Short Description The short event description that appears on the event that is raised
- Event Long Description The long description that appears in the event
- Auto Action Select an action to run automatically when the condition of raising an event is met. These are actions that have been created for the Application.
- Close event if auto action runs successfully This check box closes the event if the command exits with a successful 'error code'. For instance, the ping command on a Mac returns an error code of 0 for success and 2 for a ping failure. And the ping command on a windows OS in a command prompt returns 0 for success and 1 for failure.
- On Windows, after running the command, run the below command to see the error code that the command exited with
-
C:\users\Muuss\echo %ERRORLEVEL%
- EVENT ACTIONS These actions are available to be run by any user that has the "Run Action from Event" permission. Unlike normal actions it does not rely on the Action "Level" permission of Operator, Power User or Administrator
- HELP TEXT This text appears on the event in the "Help" section.
- NOTIFICATION WORKFLOW Select the Notification Workflow that will be used for notifications and escalations.
2.4 Node Overrides
One policy can run on multiple nodes using the same conditions to create events. Individual nodes may require different threshold values in these conditions for effective monitoring. This is known as a "Node override condition".
This is currently not enabled.
2.5 Schedule
TYPE
- Basic Run the policy once per minute or once per hour
- Time of day Run the policy once her day
- Custom Run the policy on a complex schedule
EVERY
- Basic Select "Minutes" or "Hours" and type when on the minute or hour the policy should run.
- Time of day Select hour and minute and the weekday(s) that the policy should run.
- Custom Select "Minutes" or "Hours" and type when on the minute or hour the policy should run. Select the time range when the policy should be active: e.g. 9:00am - 5:00pm. Select the weekday(s) that the policy should run.
2.6 Audit Log
DATE/TIME The date/time that the audit event occurred
USER The user that initiated the audited event
EVENT A description of what happened to the policy. Blue text indicates that it is a link to the described item.
ACTION If an action is available for the audit item it can be initiated here. For instance, roll back the policy to the previous version or restore the accidentally deleted policy.
2.7 View Data
SELECT YOUR NODE Use the drop down list box to select the node that it is deployed to. Graphs will then be visible in the below space that contains the metrics that have been collected over the last hour.
NOTE: Only nodes with this policy currently deployed are able to be selected.